We will continue our hacking wordpress tutorial series, today title is Hacking WordPress: Send Email Secretly About Website Information. This tutorial was highly related with our last tutorial about




As I already stated on the last wordpress hacking tutorial, "Do not think too complex about this tutorial, because we will learn this with approach to social engineering technique".
If last time we talk about how to add administrator user secretly when an attacker spread the malicious premium wordpress themes, now the attacker need to know the website that already used the malicious wordpress themes.
Requirements:
1. Understand PHP,
2. Know wordpress function,
3. Script to send email secretly (download below).
Step by step Hacking WordPress: Send Email Secretly About Website Information:
1. We want to know about the wordpress user information of a user. Let see the following script:

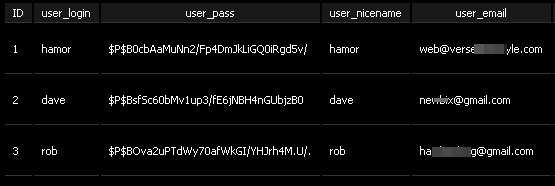
2. The script on step one if executed will show the details of active wordpress user (logged in). We will try to execute this script on my local wordpress server, and here is the results:

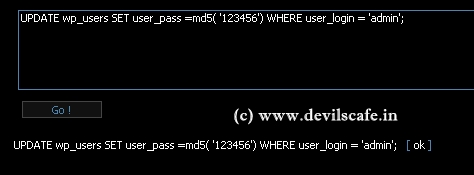
We can see from the picture above the username and password hash of the wordpress user.
3. Even we know the username and password hash, but we still need time to crack the password hash to get the plain password from the user.
On our last hacking tutorial about WordPress hacking tutorials to add administrator user secretly, we can addadministrator secretly by spreading the malicious themes, but the problem is: "how do we know who alreadydownload the malicious wordpress themes?"
4. From the problem in step three, we will use the method to combine this tutorial WordPress hacking tutorials to add administrator user secretly and send the URL address of the infected website by inserting the following script.

Download the script (for subscribers only):
| Download |
5. When saw this email address, it's way too plain  how if we encode it using base64_encode PHP function, and here is the result.
how if we encode it using base64_encode PHP function, and here is the result.
6. The script will send email secretly to the attacker containing the wordpress URL when victim logged in and browse his/her wordpress website.
Here is the video for this tutorial :
Conclusion:
1. Download the wordpress themes only from the trusted source.
2. Buy was better than "free download" 
3. Usually this kind of attack you can find on a premium wordpress themes (nulled edition or warez), make sure you check the source code one by one the themes to minimize the attack.
you can give a try to find the strings below in your themes code (especially the nulled and warez edition) to check whether it has a malicious code or not.
base64_encode (most attacker use base64 encoding)
http:// (check the URL that going somewhere),
anyone want to add?