Complete SQL injection tutorial with Havij

Hello friends. This is my third post on SQL injection and for the first
time I am using a tool for explaining it. Here I will be using a popular
and my personal favourite SQLi tool Havij. To download Havij visit the
following link - DOWNLOAD HAVIJ...
Learn Hacking by Doing-Practical Hacking Lessons with DVWA

There is always a question that people ask me is how to learn hacking.
Well I have tried my best to always find a good answer to this question,
but I have always failed. The biggest reason is that hacking is not
like a programming language that can be learned in few days or months.
It requires a continuous effort. You cannot learn it by doing a course
from NIIT or Appin. You cannot learn it by simply going to google and
type "learn hacking"...
Hacking Facebook Applications - A HackingAlert Exclusive case study!!

Recently I had the honor to write for an upcoming magazine on hacking
and Network security which is going to be launched this month. The chief
editor of the magazine is a real hard working guy and he asked me to
submit an article(cant name the topic). I went on to make some research
on the worlds biggest laboratory ( internet :) !!)..Yes internet can be
the world's biggest lab, at least for me. I was playing with the
Facebook documentation...
Complete guide to defacing a website - CookBook!!
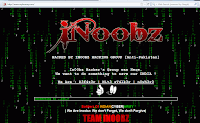
Please use this post for educational and penetration testing your own
website only.
Disclaimer: The methods and shell upload shown in this tutorial were
tested on a hacked website, so hackingalert is not responsible for any
damage.
Special Thanks to Team Innobz for the shell upload (love you guyz).
Hello friends . In the recent time I was quiet busy with my own stuff
so couldn't post cool hacking articles.
So I kept...
Understanding Honeypots - The Trap!!

First thing any hacker would do to compromise any network is gathering
information passively and seeking vulnerable services as well as ports.
And this is where Honeypots play a role of fake vulnerability in
network.
Honeypots are fake theoretically, but not practically. They are real
vulnerabilities in Network intentionally kept open & designed to
gather information about the possible attack / attacker...
Intercepting HTTP request/response using WebScarab to hack Web Applications
Hello Friends.
Recently I am really busy with my interviews in different companies. But
there is always a new thing that you can learn from everything. Though
my tough time has not yet ended but still I took out time to write this
post as there is somthing new that I learned while I was preparing for
one of my interviews for MicroWorld that is amongst the leading
companies in the field of Network Security.
The best thing I find about...
5 phases of Web Application attack - A HackingAlert Exclusive research!!

Tweet
Web
applications are now the next big victim after games for hackers .
A recent research shows that 70% of vulnerabilities exist at the top
layer of the web application.
The attackers use several techniques to hack web applications . I have
been constantly monitoring different types of web attacks involving
different methods but there ar some common steps which all hackers
follow in order to perform their attack on applications. I am
presenting...
Some FAQ's that you must know about hacking .

Tweet
I
get lots of emails from anonymous people who ask me to hack a facebook
or gmail or live account and they are also willing to pay for it too . I
never reply to such mails because of the obvious reason that "hacking
is not dirty" . You just cannot use your tricks to fool others and steal
their information . Everyone loves his/her privacy .
But there are some good questions too . Some eager learners ask me very
good questions...
How to hack a website/web server - 3 step guide.

Tweet
I
get lot of mails from people who ask me two questions very frequently;
First is "abhinav can you hack facebook,gmail,orkut etc" and the second
is "how can i hack a website" .
The first question is very irrelevant as there are no defined techniques
to hack such secure sites . You can only hack someones account only by
making the victim to commit some mistake like making the victim to enter
informations in a phishing page etc . The second...
Step 3 - Gaining access to the server/remote host through vurnabilities.
Tweet
This step involves gaining hidden access to the remote system by
exploiting the vurnabilities that are there in various different
services of the host .
To gain access using the vulnerabilities found you can use METASPLOIT .
This is a popular exploit scanner and execution tool .
Metasploit provides useful information and tools for penetration
testers, security researchers, and IDS signature developers. This
project was created to provide information on exploit techniques and to
create a functional knowledgebase for exploit developers...
Step 2 - Enumeration and scanning for vulnerabilities
Tweet
This is the next step to hacking a website or a web server . This step
involves gathering information about the web host that can be utilized
to find loop holes or errors on the services running on the server.
In order to find out what services are running on the perticular web
server and what are the open ports on the perticular server we use a
very popular tool called NMAP . You can download NMAP from the following
link.
This tool will scan the server and will give you information about all
the services running along with the version...
step 1 - Gaining information
Tweet
This is the most basic step that deals with gaining information about
the perticular website/server .
One can manually gain information by popular techniques like banner
grabbing .
You can do a manual information check on the target server . This is
known as Reconnaissance.
Active Reconnaissance involves probing of network to detect accessable
hosts , open ports , location of routers etc . You can find all
available ip addresses so that you can perform the next scanning
phase...


